



PLC chip ISP disabled
In the industrial and embedded systems fields, PLC (Programmable Logic Controller) chips are used as control cores. With the continuous development of smart manufacturing and the Industrial Internet, the functions of PLC chips have become more and more powerful, often integrating rich peripherals and communication interfaces. The chips also have ISP for firmware updates/debugging. But in some cases, the ISP function on PLC chips is disabled by chipmakers or users for security and stability. This method is a technical need yet suffers from administrative and maintainability problems.
1. Overview of ISP
ISP enables on-chip flash programming or updating of the chip’s firmware without needing to take an IC off the board for flashing via either UART, SPI, USB, or JTAG/SWD interfaces. The benefit is that it makes programming, debugging, and maintenance easier without complex programmer's operations.
ISP is commonly used in PLC implementations for the purpose of:
- Firmware updates and bug fixes
- Online debugging and functionality upgrades
- Automated programming during mass production
ISP also, however, leaves the chip’s interfaces open, which can be security risks in industrial control scenarios.
2. Reasons to Disable ISP
- Security Requirements
- Industrial control systems usually function in high-risk environments like power grids, chemical factories, or rail conveying. Since the ISP interface of the PLC can be used to send commands, hackers can potentially rewrite firmware and modify PLC logic, leading to accidents. One method to stop such attacks is the deactivation of ISP.
- Preventing Operational Errors
- Staff in the production or maintenance fields mistakenly erasing the firmware accidentally through ISP tools result in a system halt. Disabling ISP mitigates this risk.
- Protection of Firmware Intellectual Property
- Core algorithms and control logic are implemented within PLC firmware. If the ISP is publicly available, it can be reverse-engineered or pirated. Shutting down this ISP interface also provides IP protection.
- Stability and Reliability
- Sometimes ISP eats up system resources or could be influenced by EM. Disabling of ISP reduces risk, recovery, and settlement exposure.
3. Common Methods to Disable ISP
- Chip-level Option Bytes / Fuses
- Some PLC chips (such as ARM Cortex-M MCUs) have option bytes or fuse bits to disable debugging, ISP, etc. Once the feature is disabled, it cannot be re-enabled without wiping the chip.
- Software-level Protection
- Bootloaders can implement authorization (e.g., making a key code necessary to enter ISP mode). Under invalid authorization, the chip runs the user program without any interference.
- Hardware-level Blocking
- The ISP pins could either be tied to determined voltage levels or downright disconnected to stop any possible way of programming.
- Security Chip Integration
- Some advanced PLCs are using external security chips for double authentication when downloading firmware. Unauthorized attempts are blocked.
4. Impacts and Countermeasures
ISP makes the device more secure and requires some annoyances:
- Firmware updates are deteriorated: There is no way to add a bug fix or feature enhancement over ISP, which forces either chip replacement or some kind of remote update.
- Higher maintenance cost: On-site installation and debugging are more difficult, increasing after-service costs.
- Lower flexibility: More awkward for R&D and small-batch manufacturing.
The standard phased approach is followed:
- Live with ISP on during dev and tests so you can easily debug.
- Can be turned off when in formal mass production to avoid safety and stability issues in some customer engineering environments.
If your systems need to be updatable remotely, use IAP (In-Application Programming) or OTA and encrypt it and make it authenticated.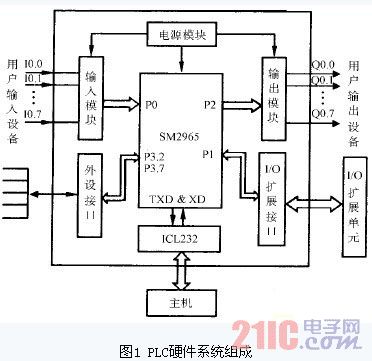
5. Future Trends
The emergence of industry security and domestic PLC chips made disabling ISP measures more intelligent:
- Safe download protocol – by integrating TLS and AES, extra layer protection wares may be used, even if ISP interfaces are open.
- Hardware-software integrated security: SoCs that come with Secure Boot and TEE, now traditional ISP protocols can be totally replaced.
- Hierarchical access control: PLC chips of the future are likely to allow application-dependent flexible policies, such as “read-only debug” or “time-limited ISP.”
Conclusion
Turning off ISP on PLC chips is a balance of security and flexibility. It plays a significant role in preventing external attacks, operational mistakes, and loss of intellectual property to ensure the stability of industrial control systems in the long run. As secure download protocols or encryption technologies are further improved, the ISP shutdown will eventually become an intelligent and sophisticated security management method rather than a complete shutdown, which is expected to provide high-level protection for industrial automation systems.

Please contact us if the source is mislabeled or violates your legal rights.
We will promptly correct and delete, thank you.









.9246509.png)












[email protected]
7500A BEACH ROAD #04-307 THE PLAZA SINGAPORE (199591)
RM 705.7/F.FA YUEN COMM BLDGNO.75-77.FA YUEN STREET.MONGKOK.KLN.HONG KONG
